Technology is changing at a rate that most institutions cannot keep pace with; hence, introducing a large that makes organizations susceptible to cyber breaches. To counteract this growing complexity, risk management strategies have also become more sophisticated. Moreover, security leaders are inclined to apply best-practices approaches to the diverse risk portfolios using concepts, such as layered security technology.
For instance, according to Singh, Aggarwal, Rajivan, and Gonzalez (2019), phishing attacks, the oldest form of security attack, have increased both in quantity and sophistication. In the current digital era, most networks are designed to operate via third-party vendors and trusted partners; most of them are connected to the cloud and share data centers (Abraham, Chaterjee, & Sims, 2019).
Chief Information Security Officers (CISOs) are thus forced to review strategic cybersecurity plans periodically. The plans describe the manner through which installed security programs will minimize cyber risks in the spheres of protecting shared data and countering evolving threats. This cybersecurity strategy aims to offer a platform for endorsing effective practices that will help achieve goals of data protection and optimized risk management.
Cybersecurity Threats in the Healthcare Sector
The effects advent and evolution of technology have also been witnessed in the healthcare sector. Healthcare institutions are increasingly adopting the utilization of smart medical equipment and mobile devices, which makes them more prone to cyber breaches. The complexity and size of hospital operations, together with the existence of several conventional and outdated systems, further hinder the employment of effective cybersecurity strategies.
As a result, this leads to the embrace of the “if-it-is-broken-do-not-fix-it” notion among high-level healthcare managers (Abraham et al., 2019). The existence of compliance regulations, federal and state healthcare laws, and the security guidance framework further complicates the sphere of cybersecurity and often effects in the management presuming a state of blissful ignorance. This strategic plan functions to assist healthcare organizations minimize cybersecurity threats in a cost-effective and all-rounded manner. This will be achieved by providing actionable, feasible, and relevant cybersecurity advice that applies to healthcare organizations of all sizes.
Cybersecurity Strategic Planning Governance
For an in-house cybersecurity strategic plan to be successful, it has to involve a high-level employee, which in this case, it is recommended to be sponsored by a Chief Information Officer (CIO). This position is most suitable as it is among the high-level managerial position; therefore, this minimizes the likelihood of the development and successful implementation of the cybersecurity plan from being mired in internal politics (Smallwood, 2014).
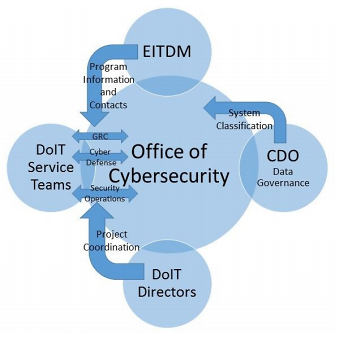
The recent rise of enterprise Information Technology (IT) decision management strategies and data governance have established the need for cultivating essential relationships within the Office of the CIO. The CIO should be seconded by the Chief Data Officer (CDO). The CDO facilitates the creation of a detailed data classification, which will allow for appropriate classification, thereby directing the selection of security controls and testing criteria. The Enterprise IT Decision Management (EITDM) team will ensure that all new or modified systems are in alignment with architectures and interfaces to improve cybersecurity.
The Office of Cybersecurity will also partner with the Division of Information Technology (DoIT) to coordinate the functions of security testing, risk management, governance, cyber defense, and compliance. Other required personnel include a representative from the legal staff, and Information Governance project manager, a risk management specialist and a senior records officer (Smallwood, 2014). Depending on the scope of the strategic plan, a team of employees from specific business units, the human resource and the communications department might be recruited (Smallwood, 2014).
Functions of CIO – The Executive Sponsor
Overall, the function of a CIO at the onset of developing a cybersecurity strategic plan is to champion its implementation, improvement, and expansion. This is in regard to portfolio and resource management, project management, listing, and roadmap management of new technology requests. The CIO works collectively with other departments, including the administration, management, and other service providers to update and modernize existing systems. Some of the CIO functions relevant to the development of a cybersecurity strategic plan include:
- Aligning various IT programs designed with the department’s strategic goals and objectives via the creation and implementation of an IT strategic plan.
- Identifying and prioritizing technology investments, sponsoring and shepherding the resources required to deliver them.
External Factors
Trends in the Cybersecurity Industry
Over the past decades, technology has evolved such that several recent cybersecurity threats have been set in motion. These include the cloud, mobile, and artificial intelligence, which are but a few trends that will continue to be exploited by black hats. Coupled with the rapid evolution of various software and shortage of cybersecurity experts, threats are expected to keep cybersecurity personnel alert.
For instance, it is presumed that ransomware, which was the scourge of 2019, also to be utilized in 2020 (Mareichev, 2019). Secondly, mobiles are anticipated to become the commonly used phishing platform for credential attacks in 2020. This is because the conventional secure email gateways are effective in blocking potential malicious URLs and phishing emails, which functions for protecting corporate email from account take over attacks. However, they fail to consider mobile attack vectors that comprise social networks, personal email, and other messaging platforms, such as SMS/MMS.
Third, as software development intensifies, so does the need to prevent cybersecurity threats at an early phase (Mareichev, 2019). This is because the attack surface has shifted from the local code to pipeline code. As a result, future code inspections will be required to begin from app inception to production. Currently, various organizations have started to build security into each stage of the development pipeline, and the number is expected to grow. Fourth, the focus of black hats is presumed to shift as more corporate infrastructure moves towards the cloud. The primary advantage that this trend offers is the performing an attack will become more challenging; nevertheless, the actions of threat actors will become more frequent and sophisticated.
Fifth, authentication will move from a two-factor to a multi-factor, which consists of biometrics (Mareichev, 2019). Most organizations use one-time authorization codes to provide two-factor authentication; however, they have remained subject to advanced phishing attacks. Therefore, to address regulatory compliance and protect themselves against the threats, the organizations are increasingly implementing multi-factor authentication and biometrics using mobile devices.
It is essential to note that although data security is heightened, mobile devices are not entirely free from compromise. Sixth, propelled by the relatively high cost of sophisticated malware attacks, including time and skill, an escalation of insider attacks has been forecasted from 2020. Consequentially, there will be a growth in the number of attacks utilizing social engineering methods, as the human factor remains the weakest link in security.
Last and most importantly, the development of 5G networks and adoption of Internet of Things (IoT) devices is prone to increase vulnerabilities to large scale multi-vector 5th generation attacks substantially (Mareichev, 2019). The global adoption of 5G infrastructure technology is expected to begin in 2020. This will result in an uptick in edge computing and an introduction for newly connected IoT devices.
Furthermore, considering that there are already some previous issues magnified by the massive 5G buildout – authorization, confidentiality, authentication, availability, and data security – organizations will have to re-evaluate their risk paradigm for connected devices. IoT connections and their devices are still a weak link in cybersecurity. This ever-increasing volume of personal data will require protection against security breaches.
Data Governance – Legal, Regulatory and Political Factors
The increasing occurrence and sophistication of cybersecurity breaches require a holistic preventive approach. Therefore, it is essential to identify the relevant laws and regulations impacting the governance of information. In a healthcare setting, these might comprise personally identifiable information, patient health records, and copyrighted research. Restricted data sets include birth date, Social Security Number, gender, phone number, and address, among others; patient health information and data protected by the Health Information Technology for Economic and Clinical Health (HITECH) Act, and Health Insurance Portability and Accountability Act (HIPAA) (Kruse, Smith, Vanderlinden, & Nealand, 2017).
On the other hand, the management of security controls, as stipulated in various research by the Clinical Research Ethics Committee, provides a basis that can be leveraged across institutions to stimulate improvements in cybersecurity and improve the protection of essential data, thereby, minimizing risk.
This plan aims to compare cybersecurity and data governance standards in the industry to offer valuable insight into the best practices that can enable health institutions to achieve their long-term objectives for internal controls. The primary outcome of establishing data definitions is the capability to allot security controls centered on the attributes of integrity, confidentiality, and availability of data. With regards to information category, confidentiality can be rated from restricted to the public; however, integrity and availability vary with the notion of the risk of exposure of the system having an increasing potential for damage should the data be compromised.
Cybersecurity Best Practices in the Healthcare Industry
Most healthcare workers are unaware of the various phishing techniques utilized. Therefore, since black hats continue to use emails and website URLs as their weapon of choice, healthcare institutions must establish and implement a simulated phishing program (Dodson & Crank, 2020). By showing employees the different types of attacks, this training program will enable them to gain the ability to identify, avoid, and report social-engineering threats that compromise critical systems. The simulations can mimic voice phishing, SMS, and email phishing.
Secondly, healthcare organizations are required to modernize their third-party risk management process (Dodson & Crank, 2020). From a compliance viewpoint, HIPAA regulations dictate that covered institutions execute third-party due diligence as it correlates to electronic patient health information; however, it does not precisely specify the manner of doing it. As a result, it is critical for healthcare organizations to establish robust governance and a suitable risk-based model that serves an essential purpose. Third, healthcare institutions often perceive that independently, technology can provide a solution to their problems (Dodson & Crank, 2020).
Consequently, they end up purchasing technical point solutions without giving much thought to the management of such tools. This further cements the misconception that the system is more protected than it actually is. Such organizations should keep in mind that the value of technology lies in how it is monitored and managed over time.
Lastly, healthcare institutions should make additional investments in endpoint solutions to safeguard their threat landscape at the edge (Dodson & Crank, 2020). Endpoint protection is described as the process by which devices, such as medical devices, medical-record systems, and payment processing systems are secured.
Cybersecurity Strategies
The achievement of this cybersecurity strategy is dependent on the capability of the Cybersecurity team, DoIT, all the organizational staff, and administrators to collaborate and communicate effectively.
Strategy 1: Establishing a community of cybersecurity experts and improve health worker competence via security education and awareness
The human factor is the weakest link in a security system, as uneducated employees can fall victim to phishing attacks. Therefore, there is a greater need to educate people by implementing training programs that enable them to become conversant with their IT security responsibilities and how to properly utilize and secure the IT devices given to them. An effective cybersecurity training program is that which outlines the proper behavior revolving around the use of IT resources, and the consequences that may arise due to non-compliance.
Actionable plans – Various security operations team identify the best industry practices and determine the costs and effectiveness of the implemented security operations.
Intended outcomes – The common employee-targeted cyber breaches are well understood. Moreover, this will be assessed by conducting phishing campaigns biannually for various departments. Successful implementation of this training will be characterized by the steady decrease in the number of employees failing on the phishing tests.
- The cybersecurity departments in various healthcare organizations will design a website or a section of a website through while the present health workers can visit for security information. This heightens IT security awareness.
- Healthcare organizations have access to the right cyber skills and talent.
Linking to healthcare organizational goals and objectives – The following show how this strategy links to organizational objectives:
- Create a conducive environment through which hospital employee can perform their responsibilities.
- Nurturing the growth of its professional community through training and performance excellence.
Strategy 2: Establishing a proactive approach against cyber breaches
Digital devices and controls are needed to achieve compliance at a magnitude set by industry standards. Furthermore, directed and constant surveillance of healthcare systems and networks will enrich the entire cybersecurity picture. It is essential to utilize an integration of both conventional and modern tools, such as anti-malware or anti-virus applications, endpoint management, cryptographic tools, firewalls, configuration and patch management, and file integrity tools, among others. The recognition and valuation of the degree of impact for various cyber risks are enhanced through measuring the efficacy of deployed services and situational awareness.
Actionable plans – The following are the actionable plans:
- The Monitoring and Incident Response Cybersecurity (MIRC) team can design an alert dashboard through which all employees with access to the system can be alerted in case an intrusion is detected.
- The MIRC team will add extra external data feeds that function to uncover suspicious activities that cannot be detected by existing sources.
Intended outcomes – The strategy goals include:
- Access to healthcare systems be limited to relevant authorized users.
- Employees’ cybersecurity awareness exceeds that of the previous year.
- There is rapid identification of vulnerabilities, impacts understood and relevant mitigations applied.
- Cyber services are regularly updated and in-built to system designs.
Strategy 3: Establishing security metrics, optimizing services and promoting compliance
Security metrics are formulated to convey security posture. This comprises potential risks to cyber operations, the confidentiality of sensitive data, and data integrity. This can be achieved by assessing the status of security controls using metrics that are sufficient enough to provide actionable results that can be communicated to stakeholders and aligns with the organizational risk tolerances. Therefore, through the collection and communication of security metrics, cyber experts are able to confirm that security controls are working as designed; detect emerging trends and threats; guarantee compliance to relevant standards, regulations, and policies; and ensure that proper funding is allocated to effective security programs.
Actionable plans – They comprise
- Creation of a budget model for every cybersecurity service present in organizations.
- Identifying the type of metrics to be collected to ensure the achievement of the intended outcomes.
- Establishing a framework continuous diagnostics and mitigation using the present tolls while evaluating for requirements and acquisition strategies for a set of tools.
Intended outcomes – Presence of appropriate and quantifiable security metrics.
Strategy 4: Enhancing collaborations and partnerships
Healthcare institutions are expected to closely work with third-party vendors to enhance expertise, learn best practices and collaborate on cyber threat prevention and mitigation strategies, policies and regulation initiatives.
Actionable plans – They entail:
- Working together with the identified third-party vendors to explore measures of enhancing the quality of cyber security services.
- Enhancing information sharing and co-ordination among individual peer organizations.
Intended outcomes – They are:
- Proper and effective cyber resilience systems are implemented.
- Information sharing protocols among peers are in place.
Supportive operational and enabling programs
For the successful achievement of the above-mentioned long-term strategy, the following near-term objectives have to be implemented:
Objective 1: Creation and nourishment of a culture which appreciates information security and actively works to minimized the risk level
All electronic devices used in healthcare institutions should comply with the industry’s accepted best practices. All endpoint devices in various institutions:
- Should have installed antivirus software that centrally report the findings.
- Should be often patched.
- Should be shielded by a centralized registered network firewall.
Objective 2: Centralizing data collection to allow for easy analysis of security related events
The cybersecurity department will be required to aggregate and centrally oversee operational data to facilitate the development of appropriate security metrics, effective security monitoring and incident response. The main elements of this objective include:
- Regularly conducting vulnerability scanning processes to identify systems at risks.
- Execution of an improved security monitoring system to increase network visibility.
- Employment of an enhanced event logging infrastructure through which departments can send operational events.
Objective 3: Compliance requirements imposed by regulatory agencies
To attain this objective, the cybersecurity team is required to identify compliance regulations that might be imposed on sections or whole of the healthcare system infrastructure. This is followed by collaborating with the data governance team to determine which standards apply to what data classifications.
Conclusion
Although given less consideration, the healthcare industry is also subject to cyber security breaches, and this can adversely impact such institutions with regards to finances lost or poor delivery of care. With the trend and direction that technology is heading towards, every industry regardless of its activities is susceptible to the growing cyber risks. Therefore, there is need to create a feasible strategic plan that can help healthcare organizations revamp their cybersecurity system and minimize risk.
References
Abraham, C., Chaterjee, D., & Sims, R. (2019). Muddling through cybersecurity: Insights from the U.S. healthcare industry. Business Horizons, 62(4), 539-548.
Dodson, D., & Crank, W. (2020). 2020 Horizon report: The state of cybersecurity in healthcare. Web.
Kruse, C. S., Smith, B., Vanderlinden, H., & Nealand, A. (2017). Security techniques for the electronic health records. Journal of Medical Systems, 41(8), 127.
Mareichev, P. (2019). Corporate security prediction 2020. Web.
Singh, K., Aggarwal, P., Rajivan, P., & Gonzalez, C. (2019). Training to detect phishing emails: Effects of the frequency of experienced phishing emails. Proceedings of the Human Factors and Ergonomics Society Annual Meeting, 63(1), 453-457.
Smallwood, R. F. (2014). Strategic planning and best practices for information governance. In Information Governance for Business Documents and Records (Chapter 5). New York, NY: John Wiley & Sons.